Side channel is the security term for using side effects to glean information that someone is trying to hide.
We all use such side channels in our day to day life. We can tell someone is nervous from their body language. We might find a hiding person thanks to their protruding shadow.
Security systems generally rely on certain data, usually keys, being kept secret. Sometimes, though the key is stored securely, a side effect of the usage of the key can be used to reveal the key. A classic example of this are power analysis attacks which utilize a device's power consumption when performing cryptographic operations with a key to deduce the value of that key.
Two novel side channel attacks have been recently announced. Both of these attacks aren't too practical - but they are quite interesting.
Schneier links to a paper that shows how a mobile device's motion sensors can be used to identify a password being typed in to the device touch screen. When you press any key on the device you move the device in a particular way that is unique to that key. So if you're running my app on your device I can use the device's motion sensors to get the bank account password that you typed in another app. This attack isn't very practical yet (the information isn't accurate enough) but it's very cool.
The H sites another paper (in German) that describes how electrical power usage can be used to detect which program you're watching on TV. Previous papers showed how power usage can be used to glean information on a person's routine, but I believe this is the first time someone has used this to determine such details as which movie you've been watching. Scary.
Thursday, September 22, 2011
Sunday, September 18, 2011
HDCP: Cool New Hack
In the previous post I mentioned the fact that the HDCP master root key was publicly revealed about a year ago. Last week Nate Lawson, on his root labs rdist blog, pointed out that the Chumby NeTV is probably the first commercial use of these leaked keys - and it's a very cool hack indeed.
The Chumby Wiki describes the NeTV as follows.
According to Nate, the NeTV uses the HDCP master root key to derive the unique key set of the two devices it's connected to (the video source and the television) and calculate the key used by the video source to encrypt the content. It then uses this to key not to decrypt the content but to replace parts of the video images with it's own (encrypted) overlay data.
At first glance you may wonder why the developers of the NeTV didn't simply generate their own unique key set (based on the master root key) and used that to decrypt the video from the video source - why go to the trouble of replacing parts of the encrypted video stream?
But by doing so the NeTV developer solved several two possible issues:
The Chumby Wiki describes the NeTV as follows.
NeTV is designed to work as an add-on to video sources like Boxee, Revue, Roku, PS3, Xbox360, DVR, DVD, set top boxes, etc. It sits between these devices and the TV. NeTV's key benefit is adding push delivery of personalized internet news on top of all platforms in a non-intrusive and always-on manner.When I first saw mention of the Chumby NeTV (on TechCrunch) I wondered how it could work with HDCP secured content but I didn't take the time to consider the question more in depth. Nate did - and came back with a surprising answer.
According to Nate, the NeTV uses the HDCP master root key to derive the unique key set of the two devices it's connected to (the video source and the television) and calculate the key used by the video source to encrypt the content. It then uses this to key not to decrypt the content but to replace parts of the video images with it's own (encrypted) overlay data.
At first glance you may wonder why the developers of the NeTV didn't simply generate their own unique key set (based on the master root key) and used that to decrypt the video from the video source - why go to the trouble of replacing parts of the encrypted video stream?
But by doing so the NeTV developer solved several two possible issues:
- If the NeTV were to decrypt the HDCP protected signal from the video source it may have been in violation of the DMCA. By not decrypting this signal Chumby reduced the risk of being sued.
- If the NeTV were to use it's own key set, not generated by the HDCP licensing authority, the NeTV may have been taken out of service by some future countermeasure against illegal devices with unauthorized HDCP keys (e.g. through device revocation). Using the TV and video source's own keys prevents this.
Thursday, September 15, 2011
HDCP: (Sub)Standard Security pt.1
I owe the readers of this blog an explanation (or two). I promised to explain "Why Security Systems Fail" and so far, after more than a month, there was only one such post (on RSA SecurID).
To make up for this I'll do a series of posts on a group of security systems describing how and why they were breached. What these systems have in common is that they were each defined as a "standard" - i.e. a specification for the security system was published and was implemented by multiple parties. The first post in the series is dedicated to HDCP. Subsequent posts will cover GSM, X.509 certificates and others.
To make up for this I'll do a series of posts on a group of security systems describing how and why they were breached. What these systems have in common is that they were each defined as a "standard" - i.e. a specification for the security system was published and was implemented by multiple parties. The first post in the series is dedicated to HDCP. Subsequent posts will cover GSM, X.509 certificates and others.
Wednesday, September 7, 2011
DigiNotar: When is a secure network not secure?
The Dutch government report (PDF) on the DigiNotar hack has confirmed what I suspected:
But don't mock them. If you use a disk encryption technology like PointSec or PGP Disk and think it gives you any signficant protection, you may be making the same mistake - assuming an attack involving physical access. It's quite likely hackers already have control of your computer even though it's physically in your possession. You should do what you can to prevent network-based attacks (firewall, anti-virus), but even then you must not assume you're 100% secure. If you have anything that is truly secret just don't put it on a computer you connect to the Internet.
There's been a paradigm shift in the world of corporate security. Instead of traveling and trying to physically access the information of a single company, hackers can use technologies like Remote Access Trojans to attempt attacks on hundreds of companies from the comfort of their own home and with less risk of getting caught by law enforcement. Too many security teams, not just RSA and DigiNotar, haven't yet fully adjusted to this situation.
BTW, the full paragraph in the report begins with another sentence:
The separation of critical components was not functioning or was not in place. We have strong indications that the CA-servers, although physically very securely placed in a tempest proof environment, were accessible over the network from the management LAN.These guys at DigiNotar are living in the nineties. These days the most important attack vector by far is through the network and not physical access. DigiNotar, like many others, invested more effort in defending against the less important attack.
But don't mock them. If you use a disk encryption technology like PointSec or PGP Disk and think it gives you any signficant protection, you may be making the same mistake - assuming an attack involving physical access. It's quite likely hackers already have control of your computer even though it's physically in your possession. You should do what you can to prevent network-based attacks (firewall, anti-virus), but even then you must not assume you're 100% secure. If you have anything that is truly secret just don't put it on a computer you connect to the Internet.
There's been a paradigm shift in the world of corporate security. Instead of traveling and trying to physically access the information of a single company, hackers can use technologies like Remote Access Trojans to attempt attacks on hundreds of companies from the comfort of their own home and with less risk of getting caught by law enforcement. Too many security teams, not just RSA and DigiNotar, haven't yet fully adjusted to this situation.
BTW, the full paragraph in the report begins with another sentence:
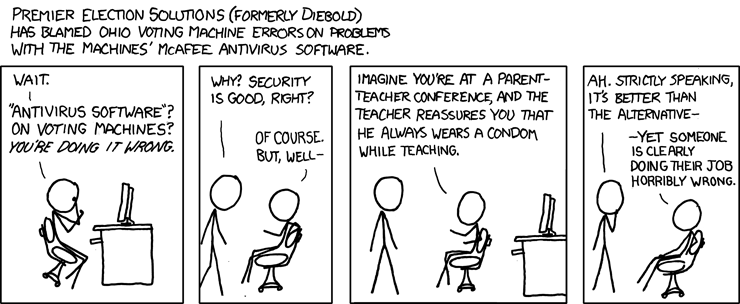
The most critical servers contain malicious software that can normally be detected by anti-virus software. The separation of critical components was not functioning or was not in place. We have strong indications that the CA-servers, although physically very securely placed in a tempest proof environment, were accessible over the network from the management LAN.Which reminds me yet again of this XKCD classic:
Subscribe to:
Posts (Atom)